Thousands of Android and iOS apps are leaking your data through their Firebase backend (Update)

Update July 2, 2018:
Google has responded to our inquiry and a bit of discussion with a member of the Google Cloud team has cleared up a few of the questions surrounding this report.
Firebase databases are secure by default when they are created and all of these cases are instances where a developer hasn't followed best practices in one form or another. Google publishes a full guide on securing realtime databases with Firebase. Additionally, the Firebase admin console displays an unmistakable warning when a database has had the normal default protections removed and is configured to allow for public access.
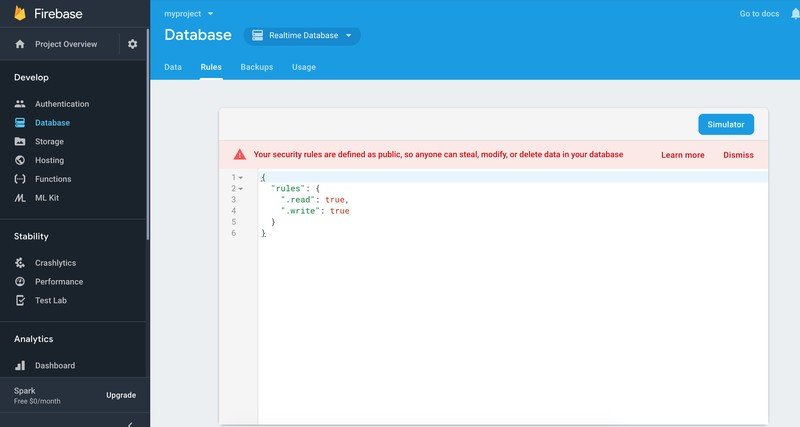
Google also tells me that emails were sent to all insecure projects with complete directions on how to turn database security back on in December 2017. It's clear after speaking with a member if the Google Cloud team that Firebase is as safe as we all had thought it was and that issues like this are attributed to developer mistakes.
The original article appears below.
Firebase is a great service for any small developer who needs to have an online service at their disposal. It's powered by Google and the company goes out of its way to help developers use it in their mobile apps. You can see by simply watching any Google I/O session video about Firebase that developers actually cheer when the service is mentioned.
Apparently, some of those developers have hit a snag when it comes to configuring the database they may be using to store your data. After scanning 2.7 million apps, security researchers at Appthority say more than 113GB of data is available through over 2,200 Firebase databases to anyone who knows the right URL. In total, there are over 100 million personal records exposed.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
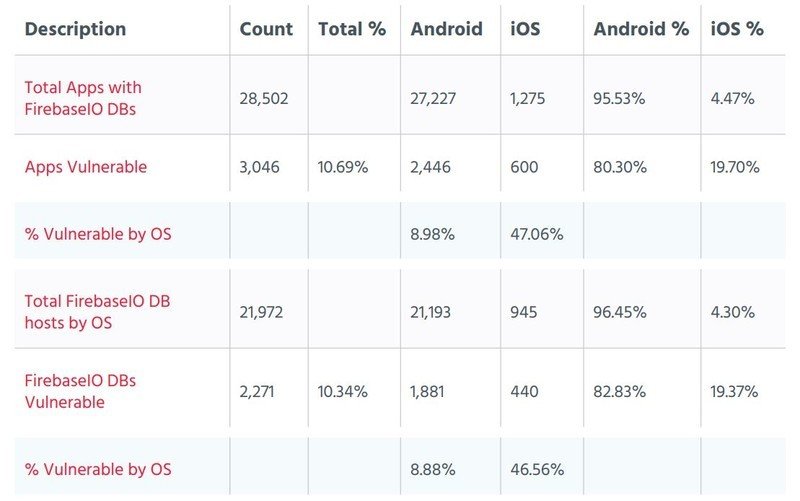
Researchers found 28,500 apps that used Firebase to connect and store user details, of which 3,046 stored their data inside a misconfigured Firebase database that was readable through the use of a JSON URL scheme. The majority of the apps that use Firebase are for Android, but 600 apps that exposed data are for iOS. The problem is platform-agnostic, and the apps in question aren't the culprit here. It's simply the database configuration on the backend.
The information leaked contains:
- 2.6 million plaintext passwords and user IDs.
- 4 million+ PHI (Protected Health Information) records.
- 25 million GPS records.
- 50 thousand financial including Bitcoin transactions.
- 4.5 million Facebook, LinkedIn, corporate data-store user tokens.
Appthority informed Google about the database configuration and provided the list of affected apps before this report was published. We've reached out to see if Google has anything they would like to add and will update once it's received.
Appthority is no stranger to finding poorly configured online databases. Previously the company has found "critical" user data exposed through services like MongoDB, CouchDB, Redis, MySQL, and Twilio.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
