The MY2022 app is a required download for Olympians and looks like a security nightmare

A while back we heard that a handful of countries advised their respective Olympic teams to leave all personal electronics at home and use a "burner phone" while in Bejing. This was, of course, done because of concerns about the Chinese government's heavy hand with the internet and all electronic communications. Sometimes, Big Brother really is watching.
It turns out that this advice was pretty solid, as researchers have torn apart the Android and iOS versions of the MY2022 app — which is required to be used by all Olympians — and found some really interesting things. Not the good kind of interesting, either.
After reverse engineering all of the #Beijing2022 #spyware app for @Apple #ios and @Google #Android
I can definitively say all Olympian audio is being collected, analyzed and saved on Chinese servers using tech from USA blacklisted AI firm @iflytek1999 https://t.co/9wX1sP8PZP pic.twitter.com/hdIfiKX37mAfter reverse engineering all of the #Beijing2022 #spyware app for @Apple #ios and @Google #Android
I can definitively say all Olympian audio is being collected, analyzed and saved on Chinese servers using tech from USA blacklisted AI firm @iflytek1999 https://t.co/9wX1sP8PZP pic.twitter.com/hdIfiKX37m— Jonathan Scott (@jonathandata1) January 26, 2022January 26, 2022
There is a lot to process in this Twitter thread, and none of it is good. Taken at face value, the code for the app on both platforms shows:
- The app takes full control of the microphone
- The app forces itself into the foreground so Android users won't get a notification that it is running
- The app can collect audio at any time
- The app sends audio files to servers located in mainland China
- The collected audio is processed by Chinese AI firm iFLYTEK, which has been blacklisted in the U.S. over security concerns
- Users of Chinese brand phones from Huawei, Xiaomi, Vivo, Meizu, and Oppo devices also send data back to the manufacturer through the app
Yikes! This doesn't give an air of confidence about using the app that China forces athletes to install on their phones if they wish to participate in the 2022 Winter Games. It's also worth noting that both Apple and Google have done a lot of work to make sure applications can't do any of this. Still, no type of security protection is ever foolproof and this is a great example. I've tried to find someone in Bejing with an Android 12 phone to see if the microphone indicators are active, but I'm not very well connected in the Olympian crowd. If you are, please take a moment to help out.
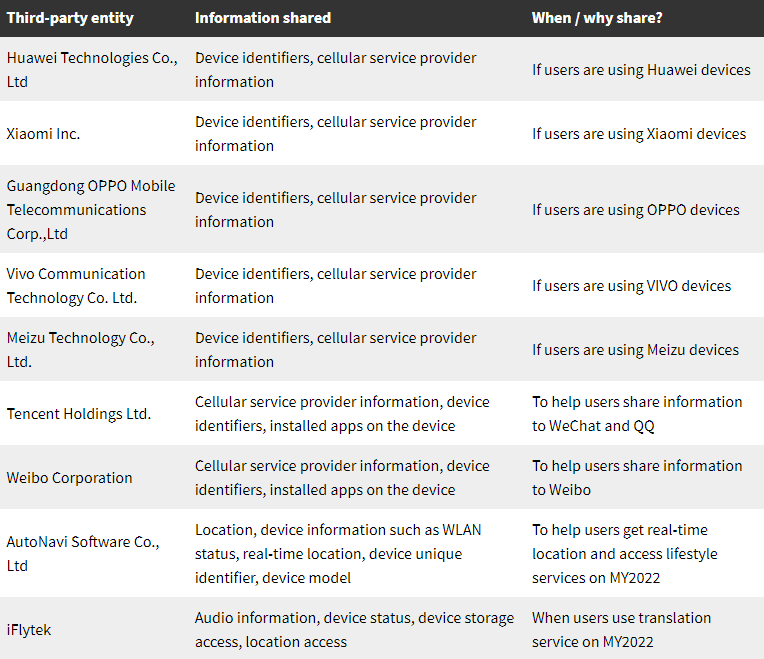
It's very important to point out the things that are 100% happening from the things that could happen. We know the audio is being processed by a firm the U.S. claims is working for the Chinese Communist Party government. It's also a Chinese startup with offices located in China.
We also know that the app is forcing its way into the foreground. If you're not aware, that means the app runs as if it is being displayed on your screen, even if it's not. It's not a great practice, but the ability is there on Android and iOS because sometimes it's a necessary evil.
We know that the audio, once captured, is sent to a server located in China. This makes perfect sense — a Chinese firm is doing the processing, and Chinese companies all have servers located in China. This isn't a great thing, but it is an expected thing.
Get the latest news from Android Central, your trusted companion in the world of Android
As for the rest, well, the app could fire itself up and record everything it hears without the user. or anyone around the user, knowing. It could then send this data to a server where an excellent AI can process it and flag anything it thinks needs to be heard by an actual human. Remember, China is a country that doesn't have any sort of First Amendment-style protections, and when inside Chinese borders, you can't just say whatever you want. Especially any sort of criticism of the government, or talk about Winnie the Pooh.
Every good story has two sides. Enter Dan Goodin, another security researcher and Ars Technica reporter who isn't quite sold on all of these claims. However, he fully agrees that the app is fishy AF and says with The Citizen Lab's assessment the app seems worrisome.
Maybe the app can do these things, but there is no proof it has or will.
He also tempers the discussion with a simple lack of proof. The app can possibly do other things, but there is no proof it has or will. He's right, too. Part of the reason is that research into the app is new, and the 2022 Winter games just started, but another part is how mobile operating system application permissions work. In the end, too many things are lumped together, and apps get permissions they do not require because of it.

Bottom line, the only real solution in this sea of scary unknowns is to use a burner phone instead of one of the best Android phones. If everything claimed about the app is true, you'll still be sending every noise you make to the CCP, but once you're done with the 2022 Winter Olympics games, you can toss the phone into a wastebasket at the airport. Most of us won't have to worry about it because we're not attending the 2022 games, but similar situations can happen to anyone traveling internationally, especially when traveling to a country that doesn't respect your civil rights in the way you're accustomed to.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.
