What you need to know about the CONFIG_KEYS Linux kernel vulnerability
A new security issue (CVE-2016-0728 for those who like to keep track of these things) was announced on January 14 by Perception Point, a security research team. The bug affects kernels compiled with the CONFIG_KEYS kernel configuration switch set to "on," and has been present in all Linux kernels since version 3.8. The exploit allows root escalation by cycling a 32-bit integer back to zero. Perception point claims that "approximately tens of millions of Linux PCs and servers, and 66 percent of all Android devices" are affected.
Google's Adrian Ludwig, lead engineer for Android security, has responded, saying the exploit has been patched and released to open source as of January 20.
As always, there are still plenty of questions. Let's talk about them.
What is going on?
There's a bug in the Linux kernel (version 3.8 and higher) that lets an attacker get root access. The kernel needs to have been built with the Keyring service enabled, and an attack needs to do a lot of math to make a number count as high as it possibly can, then go back to zero. It takes 4,294,967,296 computations to cycle a 32-bit integer (two to the 32nd power) back to zero. This takes just 30 minutes or so on a brand new Intel i7 CPU, but would take a lot longer (as in a whole lot longer) on a phone CPU.
Once the number goes the whole way around (think of how a pinball machine goes back to zero once your score reaches 999,999,999) and back to zero, the attacker can gain access to the memory space and execute code as the super user.
Should you be worried?
Get the top Black Friday deals right in your inbox: Sign up now!
Receive the hottest deals and product recommendations alongside the biggest tech news from the Android Central team straight to your inbox!
We should always be concerned when a security exploit arises. This time is no different. But there are a few things here that make many question the number of potentially affected devices.
- The recommended kernel configuration for Android devices does not have the CONFIG_KEYS variable turned on, and that means this exploit will have no effect. The people who made your phone may have enabled it, and custom ROM cookers might have, too.
- All Nexus phones are unaffected — they use the default kernel configuration and the Keyring is not enabled in the kernel.
- SELinux negates the attack vector, so if your phone or tablet is running Android 5.0 or higher, you should be unaffected.
- Most devices not running Android 5.0 or higher will be using an older version of the Linux kernel, and are unaffected.
Yes, plenty of computers, phones and tablets are affected by this exploit. But we doubt the numbers Perception Point has given.
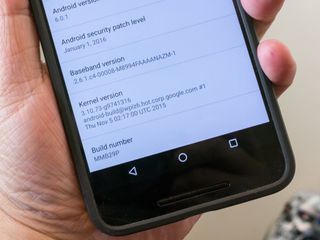
We can't audit all 11,000 different models of Androids out there, but we can direct everyone with more questions to their relevant device forum. In a nutshell, if you're running Lollipop you're safe. If you're not, look at the About device screen and check your kernel version. If it's earlier than 3.8 you're safe.
What should I do?
This is one of those security issues that can be exploited by an app — provided your phone is vulnerable as we talked about above. Because there is a lot of calculation involved, you would have to have a bad app running in the foreground for a long time, so something like a game would be a good app to try and hack an exploit into.
To stay safe, don't install apps you do not trust. Ever.
If you're not sure who you can trust, just make sure you do not allow apps to be installed from unknown sources and stick to Google Play.
It really is that easy to be 100 percent safe from this one.
What about updates for the exploits?
Google's Ludwig says that the patch was released January 20 to open source and delivered to all partners. Manufacturers will have to include this patch to be compliant with the security patch level of March 1, 2016, and later.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.