'Fake ID' and Android security [Updated]

Today security research firm BlueBox — the same company that uncovered the so-called Android "Master Key" vulnerability — has announced the discovery of a bug in the way Android handles the identity certificates used to sign applications. The vulnerability, which BlueBox has dubbed "Fake ID," allows malicious apps to associate themselves with certificates from legitimate apps, thus gaining access to stuff they shouldn't have access to.
Security vulnerabilities like this sound scary, and we've already seen one or two hyperbolic headlines today as this story has broken. Nevertheless, any bug that lets apps do things they're not supposed to is a serious problem. So let's sum up what's going on in a nutshell, what it means for Android security, and whether it's worth worrying about ...
Update: We've updated this article to reflect confirmation from Google that both the Play Store and "verify apps" feature have indeed been updated to address the Fake ID bug. This means the vast majority of active Google Android devices already have some protection from this issue, as discussed later in the article. Google's statement in full can be found at the end of this post.
The problem — Dodgy certificates
'Fake ID' stems from a bug in the Android package installer.
According to BlueBox, the vulnerability stems from an issue in the Android package installer, the part of the OS that handles the installation of apps. The package installer apparently doesn't properly verify the authenticity of digital certificate "chains," allowing a malicious certificate to claim it's been issued by a trusted party. That's a problem because certain digital signatures provide apps privileged access to some device functions. With Android 2.2-4.3, for instance, apps bearing Adobe's signature are given special access to webview content — a requirement for Adobe Flash support that if misused could cause problems. Similarly, spoofing the signature of an app that has privileged access to the hardware used for secure payments over NFC might let a malicious app intercept sensitive financial info.
More worryingly, a malicious certificate could also be used to impersonate certain remote device management software, such as 3LM, which is used by some manufacturers and grants extensive control over a device.
As BlueBox researcher Jeff Foristall writes:
"Application signatures play an important role in the Android security model. An application's signature establishes who can update the application, what applications can share it's [sic] data, etc. Certain permissions, used to gate access to functionality, are only usable by applications that have the same signature as the permission creator. More interestingly, very specific signatures are given special privileges in certain cases."
While the Adobe/webview issue doesn't affect Android 4.4 (because the webview is now based on Chromium, which doesn't have the same Adobe hooks), the underlying package installer bug apparently continues to affect some versions of KitKat. In a statement given to Android Central Google said, "After receiving word of this vulnerability, we quickly issued a patch that was distributed to Android partners, as well as to the Android Open Source Project."
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
Google says there's no evidence 'Fake ID' is being exploited in the wild.
Given that BlueBox says it informed Google in April, it's likely any fix will have been included in Android 4.4.3, and possibly some 4.4.2-based security patches from OEMs. (See this code commit — thanks Anant Shrivastava.) Initial testing with BlueBox's own app shows that the European LG G3, Samsung Galaxy S5 and HTC One M8 are not affected by Fake ID. We've reached out to the major Android OEMs to find out which other devices have been updated.
As for the specifics of the Fake ID vuln, Forristal says he'll reveal more about at the Black Hat Conference in Las Vegas on Aug. 2. In its statement, Google said it had scanned all apps in its Play Store, and some hosted in other app stores, and found no evidence that the exploit was being used in the real world.
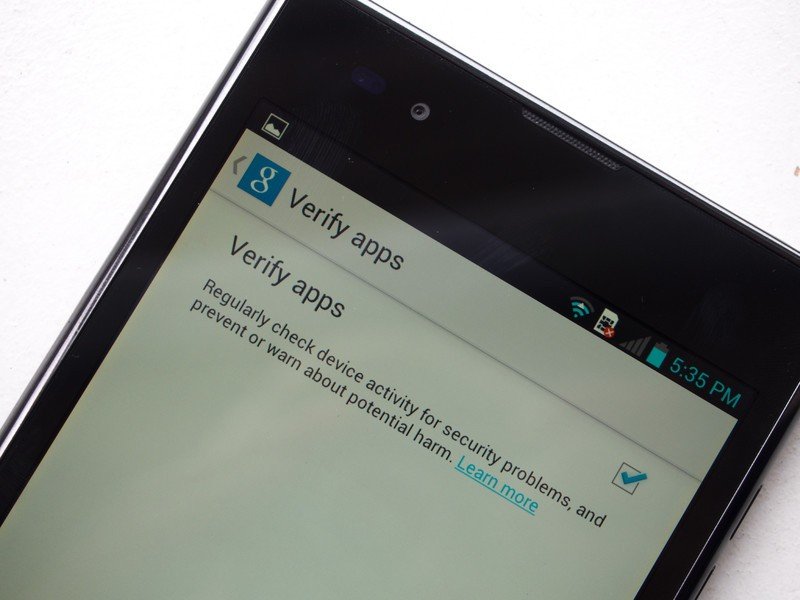
The solution — Fixing Android bugs with Google Play
Through Play Services, Google can effectively neuter this bug across most of the active Android ecosystem.
Fake ID is a serious security vulnerability that if properly targeted could allow an attacker to do serious damage. And as the underlying bug has only recently been addressed in AOSP, it might appear that the great majority of Android phones are open to attack, and will remain so for the foreseeable future. As we've discussed before, the task of getting the billion or so active Android phones updated is an enormous challenge, and "fragmentation" is a problem that's built into Android's DNA. But Google has a trump card to play when dealing with security issues like this — Google Play Services.
Just as Play Services adds new features and APIs without requiring a firmware update, it can also be used to plug security holes. Some time ago Google added a "verify apps" feature to Google Play Services as a way to scan any apps for malicious content before they're installed. What's more, it's turned on by default. In Android 4.2 and up it lives under Settings > Security; on older versions you'll find it under Google Settings > Verify apps. As Sundar Pichai said at Google I/O 2014, 93 percent of active users are on the latest version of Google Play services. Even our ancient LG Optimus Vu, running Android 4.0.4 Ice Cream Sandwich, has the "verify apps" option from Play Services to stand guard against malware.
Google has confirmed to Android Central that the "verify apps" feature and Google Play have been updated to protect users from this issue. Indeed, app-level security bugs like this are exactly what the "verify apps" feature is designed to deal with. This significantly limits the impact of Fake ID on any device running an up-to-date version of Google Play Services — far from all Android devices being vulnerable, Google's action to address Fake ID via Play Services effectively neutered it before the issue even became public knowledge.
We'll find out more when information on the bug becomes available at Black Hat. But since Google's app verifier and Play Store can catch apps using Fake ID, BlueBox's claim that "all Android users since January 2010" are at risk seems exaggerated. (Though admittedly, users running a device with a non-Google-approved version of Android are left in a stickier situation.)
Letting Play Services act as gatekeeper is a stopgap solution, but it's a pretty effective one.
Regardless, the fact that Google has been aware of Fake ID since April makes it highly unlikely that any apps using the exploit will make it onto the Play Store in the future. Like most Android security issues, the easiest and most effective way to deal with Fake ID is to be smart about where you get your apps from.
For sure, stopping a vulnerability from being exploited is not the same as eliminating it altogether. In an ideal world Google would be able to push an over-the-air update to every Android device and eliminate the issue forever, just as Apple does. Letting Play Services and the Play Store act as gatekeepers is a stopgap solution, but given the size and sprawling nature of the Android ecosystem, it's a pretty effective one.
It doesn't make it OK that many manufacturers still take way too long to push out important security updates to devices, particularly lesser-known ones, as issues like this tend to highlight. But it's a lot better than nothing.
It's important to be aware of security issues, especially if you're a tech-savvy Android user — the sort of person regular people turn to for help when something goes wrong with their phone. But it's also a good idea to keep things in perspective, and remember that it's not just the vulnerability that's important, but also the possible attack vector. In the case of the Google-controlled ecosystem, the Play Store and Play Services are two powerful tools with which Google can handle malware.
So stay safe and stay smart. We'll keep you posted with any further information on Fake ID from the major Android OEMs.
Update: A Google spokesperson has provided Android Central with the following statement:
"We appreciate Bluebox responsibly reporting this vulnerability to us; third party research is one of the ways Android is made stronger for users. After receiving word of this vulnerability, we quickly issued a patch that was distributed to Android partners, as well as to AOSP. Google Play and Verify Apps have also been enhanced to protect users from this issue. At this time, we have scanned all applications submitted to Google Play as well as those Google has reviewed from outside of Google Play and we have seen no evidence of attempted exploitation of this vulnerability."
Sony has also told us it's working on pushing out the Fake ID fix to its devices.

Alex was with Android Central for over a decade, producing written and video content for the site, and served as global Executive Editor from 2016 to 2022.
