Recent Google Wallet vulnerability could expose credit card information
Fortunately, a fix is already inbound.

What you need to know
- Recent findings have unveiled a loophole in Android, particularly with Google Wallet.
- Cards linked to the wallet risk exposing themselves if NFC and App pinning features are enabled.
- Google is said to be aware of the issue, and the recent September 2023 security patch for Android devices might have fixed it.
- The Pixel phones, however, are yet to receive the security patch.
Android screen pinning, aka app pinning functionality, is a nifty feature that lets users pin specific apps (via apps overview) on their screens. However, a recent security vulnerability has revealed that this feature can put your credit/debit cards at risk if linked to your Google Wallet.
A recent Github finding (via 9to5Google) has revealed a possible way to get your card details linked to Google Wallet through a general-purpose NFC reader (Flipper Zero, in this case). The finding suggests this is due to a logic error in the code when the device resides in lock screen mode — with app pinning enabled — and the NFC turned on. The risk is significant as user interaction isn't necessary for this exploitation.
The Github member used a Google Pixel 7 Pro with App Pinning enabled and "Ask for Pin before unpinning" turned on. At least one card has to be linked to Google Wallet. Additionally, NFC has to be enabled with the "Required device unlock for NFC" option allowed.
In this state, the phone is vulnerable as pointing a POS (Flipper Zero in this case) at the back of the Pixel 7 Pro could read the card's data (including card number expiry date) that was registered in Google Wallet.
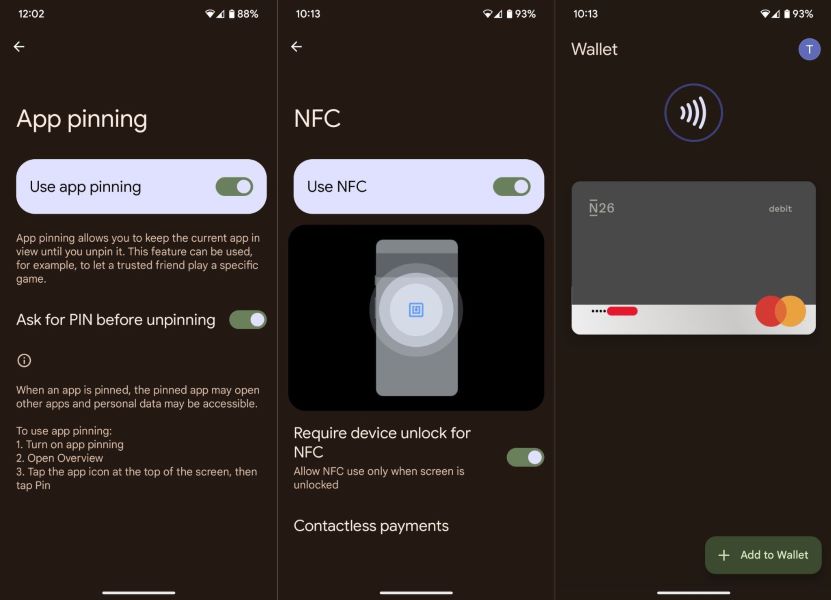

This makes it possible for anyone with an NFC reader, like the one used in the video, to obtain someone's card information. The GitHub user notes that if a real POS machine is used, there would be a higher risk of your card undergoing an unauthorized transaction without user interaction with the phone.
While an end user going through the aforementioned steps in regular day-to-day use is fairly unlikely, it's still a pretty notable vulnerability. That said, it's one that Google is already aware of, and Android devices running the September 2023 security patch should be safe from the exploitation.
Many phones, such as the Galaxy S23 series, are already receiving the September 2023 patch, although Google is yet to roll out the patch (or the Android 14 update) to its Pixel phones, including the recent Pixel 7 series.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android

Vishnu is a freelance news writer for Android Central. Since 2018, he has written about consumer technology, especially smartphones, computers, and every other gizmo connected to the internet. When he is not at the keyboard, you can find him on a long drive or lounging on the couch binge-watching a crime series.
-
fuzzylumpkin Reply
I wonder how you sleep at night... or if you're a bot, how the person who wrote you does. What a horrible person.jayhaden7 said:A special thanks to Dr udoka for curing me from stage 2 cancer, I have tested positive for the last 5 months, I have contacted him based on the testimonials I see about him on the internet, he has also cured me, Dr udoka is a great herbalist,he is able to cure all infections and diseases, 1. HPV
2. Herpes1 / 2
3. Diabetes 1/2
4. Lymphoma disease
5. Hepatitis B
6. Lupus
7. Chronic pain
8. Fibromyalgia
He also cures all kinds of human infections and diseases, you can contact him by WhatsApp: +234 913 112 7943 or via email:drudoka124@gmail.com
https://www.facebook.com/drudokaherbalcureforanysickness/ -
gomezz I just installed Google Wallet yesterday on my S20 and one thing I did was set up a Bixby routine to turn on NFC when the app is opened and turn if off when it is closed. If you like, this is similar to taking your contactless credit card out of your lined, protected wallet and putting it back in again.Reply
