Android Security — a Q&A with Google's Adrian Ludwig

We've been talking a lot about security on your Android device recently, and as the conversation continued it was clear there were questions that needed to be answered by a person a greater authority. Things like whether you need antivirus software for your phone, identifying malware, and being sure your devices are generally safe through daily use are topics that have become unnecessarily muddy. While we can place some of the blame for this on the seemingly endless barrage of articles telling us about all of the software out there being made to exploit Android users, there also are some legitimate questions about Android security that don't have plain, simple answers.
To help address this, we've gone straight to the source. Adrian Ludwig, a lead engineer for Android security at Google, took some time via email to give the answers we've been looking for.
Read more: Android Security - a Q&A with Google's Adrian Ludwig
Google's role

Q: What, exactly, is Google trying to protect its Android users from?
Ludwig: We designed Android using multiple layers of security — Starting with device hardware features (Trustzone, NX), through the operating system (Application Sandbox, SELinux, ASLR) and up to applications and services that Google provides (Google Play, Device Manager, Verify Apps, etc). We also encourage security innovation by enabling third parties to provide security solutions.
The most pressing security threats facing mobile devices these days include: 1. Lost and stolen devices (for which we provide protections like lockscreen, device encryption, and Android Device Manager) 2. Network-level attacks (for which Android provides cryptographic services and exposes a minimal attack surface by having no listening services by default) 3. Potentially harmful applications (for which the Android Application sandbox, Google Play review of applications, and Verify Apps are all designed)
When we hear about a new potential threat, we begin to incorporate that into our future plans and design.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
Support policy

Q: How long does Google offer support for things like security vulnerabilities that are discovered in the operating system?
Ludwig: Our approach to a support policy for Android security is to provide updates everywhere we believe they will actually be delivered to users and improve security. In practice this means we provide multiple different types of support for potential security issues:
- If an issue can be resolved by updating Chrome, Gmail, Google Play, or any number of Google applications — we'll resolve the issue in a manner that goes back to all Android versions on which each application is available.
- Google Nexus devices and Google Play edition devices regularly receive security updates in a timely fashion.
- We provide patches for the current branch of Android in the Android Open Source Project (AOSP) and directly provide Android partners with patches for at least the last two major versions of the operating system. Currently, we're providing backports for security issues that cover Android 4.3 and greater. WebKit on Android 4.3 is the one exception. It is supported on Android 4.4 and above as a binary update. Nevertheless, when an OEM requests assistance in developing a patch for a device that is running an older version of the platform and they commit to delivering that patch as an OTA to devices, we'll provide them with assistance.
- Where possible, we also update Google's security services for Android to provide an additional layer of protection for all Android devices, regardless of whether they are still supported by OEMs. This includes checking for potentially harmful applications and other security behavior.
- We also provide application developers with information and tools to ensure their applications are protected against potential security issues. This includes providing APIs within Google Play Services such as the updatable Security Provider that can be updated by Google without a device OTA. We also provide best practices that can help developers make sure their applications work safely on all Android devices, regardless of whether they are still supported by OEMs. Recently, we've begun to scan applications in Google Play for potential security vulnerabilities and notify developers when those vulnerabilities are detected.
- Last, but not least, we share information about security issues (including information we have about fixes and any known exploitation) with Android partners to make sure they understand the issue, including the risks associated with devices not receiving an update for the issue. This includes adding tests for potential security issues in the Compatibility Test Suite to reduce the chance that an OEM inadvertently ships a device with a known security issue.
User control
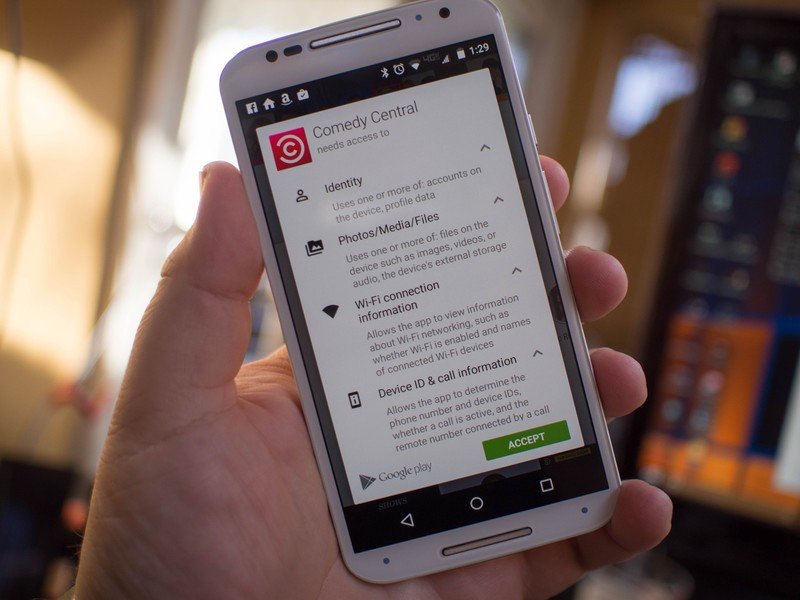
Q: In the event an app has been deemed malicious but not necessarily dangerous — for example an app that spams the notification tray with unwanted ads — what tools are available to help users?
Ludwig: Android provides users with controls that allow them to control the experience on their device. This includes capabilities like viewing application permissions, configuring settings such as the ability of an application to display notifications, or the ability to disable or remove applications at any time.
If a notification is unwanted, the user can long-press on the notification to see which app produced it and then change the application's notification settings or uninstall the application.
Security checks
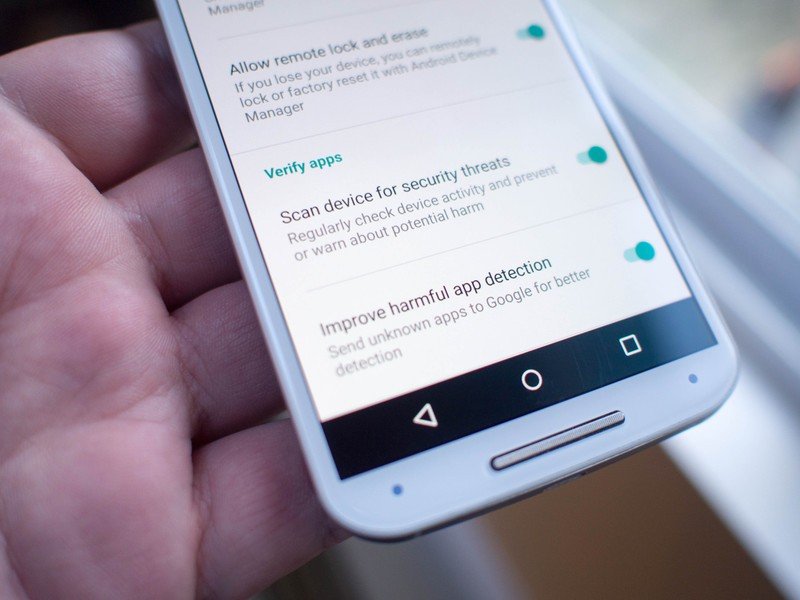
Q: What happens when Google sends a message warning users of a malicious app and the user doesn't remove the app, either because they choose not to or the message was accidentally dismissed?
Ludwig: There are multiple redundant security checks that are designed to make sure that an app that is known to be potentially harmful won't be accidentally installed. At each of these checks, the majority of users who receive a warning about a potentially harmful app choose not to proceed.
Here are all the major steps:
Google has integrated its warning system for known potentially harmful apps into the backend of many of our apps. So, for example, the Chrome browser with Safe Browsing might warn the user before they even download an app from a website that it looks like they are on a website that hosts potentially harmful apps.
If they choose to download and install anyway, they would receive a warning at install time (as well as other information such as the application permissions that can help them decide if they want to install).
If they still decide to proceed, the application is installed, but it still can't do anything until the user actually decides to run the app. So they have one more chance to choose to remove the application before it could possibly cause any harm.
Whether they choose to run the app or not, if it's installed on their device, then the Verify Apps background scanning will flag the app and provide another warning recommending that they remove the app. This warning will generally occur about once a week — though the user does have the option to say "don't remind me again."
Antivirus apps
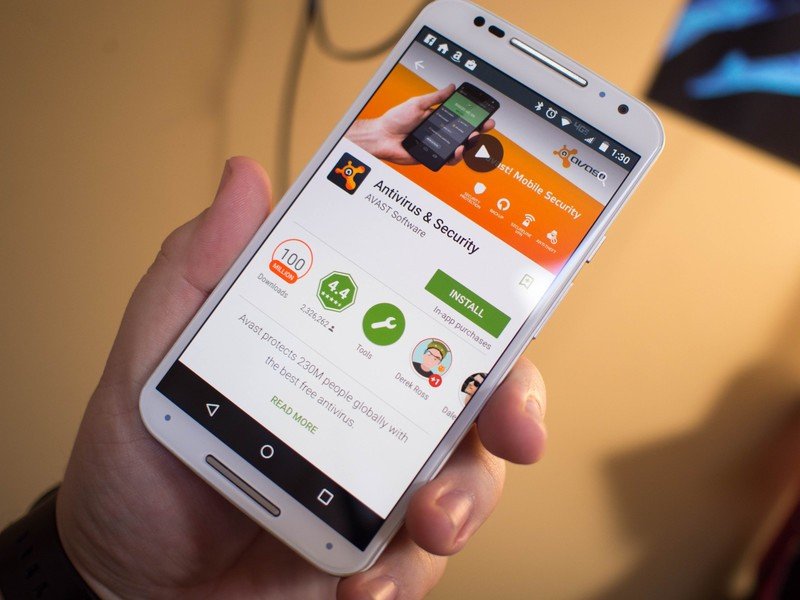
Q: Are third-party security apps keeping me even more safe from potentially harmful Play Store apps?
Ludwig: The protections built into Google Play are very robust. For users installing apps outside of Google Play, we strongly recommend they enable Verify Apps, which is provided on Android devices running Android 2.3 or greater (that's more than 99 percent of Android devices) that have Google Play installed.
In 2014, according to Verify Apps data collected by Google and ignoring rooting apps that were intentionally installed by users, fewer than 0.15 percent of Applications installed from outside of Google Play to U.S. English devices were classified as Potentially Harmful Applications. Given the built-in protection provided by Verify Apps and the low frequency of occurrence of installation of PHAs, the potential security benefit of an additional security solution is very small.
Custom ROMs

Q: Do any of Google's Security features apply to users who have installed third-party versions of Android (read: community-made ROMs)?
Ludwig: Yes, third-party ROMs are generally built on AOSP, so they support the Android sandbox, and many of them use Google's applications, including our security services.
And there you have it. Google does an incredible amount of work to keep Android safe, and a huge portion of that is being prepared for whatever happens next. But it's always going to be a bit of a cat-and-mouse game. As has always been the case, keeping your device safe is all about being aware of where you are tapping, what you are installing, and being as informed as possible.
Be sure to check out the rest of our security series if you'd like to learn more.

