How to securely access your Synology NAS from anywhere
Here's why Tailscale is the best way to log in to your NAS from outside your home network.

One of the best features of a NAS server is the ability to access your files even when you're not on your home network. Synology has robust mobile clients to access your media collection and documents over the internet, and it does so using its secure tunneling service dubbed QuickConnect.
I've used QuickConnect for several years now, and I'll provide a short walkthrough of what the service has to offer. But given the recent slate of ransomware attacks on mainstream NAS manufacturers, I decided to use a VPN to securely connect to my NAS when I'm outside my home network.
Tailscale is that VPN utility, and in this post I'll talk about how you can set it up on your NAS, and why you should do so right now.
QuickConnect: Synology's relay service gets a lot right
QuickConnect is Synology's built-in relay service that lets you connect to your home NAS over the internet. As a high-level overview, QuickConnect makes it easy to connect to your NAS without having to manually forward ports on your router.
It does this by assigning each NAS a unique ID. So when you're trying to access your media collection with DS video, instead of writing your NAS IP address, you just enter the server ID and your username and password, and you'll be able to log in.
When you're on your home network, it uses LAN detection to identify the NAS IP and connect to the server. But when you're on cellular data or trying to connect to your NAS from another location, QuickConnect sets up a virtual tunnel to see if the NAS is accessible via its WAN address.
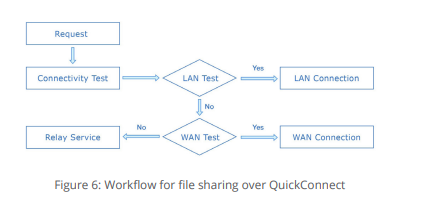
When that isn't feasible, the service leverages Synology's relay server to establish a connection between the client device you're using and your NAS. Synology has easy-to-understand documentation that talks about how QuickConnect works, and it also goes into detail about the service's security.
Get the latest news from Android Central, your trusted companion in the world of Android
In short, QuickConnect delivers the easiest way to access your NAS remotely, and it works seamlessly with Synology's first-party utilities like DS audio, DS video, DS file, and so on.
While I used QuickConnect for a long time, I wanted to use a Wireguard-based tunneling solution for increased security. So I disabled QuickConnect, and made the transition to Tailscale.
Tailscale: Access your Synology NAS from anywhere
Tailscale is a zero-config VPN that lets you securely connect to devices over the internet. Unlike a traditional VPN that relies on a central server, Tailscale uses a peer-to-peer mesh network to facilitate connections.
The best part about Tailscale is the fact that it takes less than 10 minutes to set it up. The service is based on the Wireguard protocol, uses hourly key rotation, and doesn't have any traffic going through Tailscale's servers. All traffic is encrypted by default, so you're guaranteed a secure connection. Let's take a look at how you can set up Tailscale on your NAS.
Tailscale and Synology: How to set up and use
The key differentiator for Tailscale (other than the security) is just how easy it is to set up and use. The Tailscale client is available natively on DiskStation Manager, and installing it on your NAS takes a few minutes at most. Here's what you need to do:
- Navigate to the Synology Package Center.
- In the Search box, enter Tailscale.
- Select Install.
After Tailscale has been installed on your NAS — I have it running on my DiskStation DS1522+ — you will need to log in to the service. Tailscale doesn't use its own authentication system; instead, it works with leading SSO identity providers including Google, Microsoft, GitHub, and more.
All you need to do is authenticate with your Google or Microsoft account, and do the same on any of the client devices where you want to use Tailscale.
After logging in, you'll get to the admin interface where you can see the machines that are connected to your Tailscale network (Tailnet). You should see your NAS listed here with its status showing as Connected.
You should also see an IP address next to your NAS. This is the Tailscale IP, and that's what we'll use to connect the NAS to client devices. I'm using the Galaxy S22 Ultra as the client device for this guide, but you can download Tailscale on just about any platform.
First up, you'll have to install Tailscale on Android, and once that's done, use the same identity provider you used with the NAS to log in to the service. After you log in, you'll see your phone name along with a unique IP, and the other devices on your Tailscale network, including the NAS.
Select the toggle at the top to connect your phone to the Tailscale network, and you're connected to the secure Tailnet tunnel. Now all you need to do is use the Tailscale IP of the NAS to connect to your home NAS server.
In the My Devices list, press and hold the NAS IP to copy it. Now go to DS file, DS audio, or any of the other Synology mobile clients that you want to use, and paste the NAS's Tailscale IP in the Address field.
Then enter your NAS username and password, and hit Sign In to access the server. That's all there is to it! You can use the same system for other devices that you want to use with Tailscale; just install the service, connect to your Tailnet, and use the Tailscale NAS IP to connect to your home server.
Tailscale is the way forward
I've been using Tailscale for the better part of a year now, and it's honestly been a revelation. I had zero issues using the service to access my NAS when I'm outside my home network, and the ease of use combined with the security on offer makes it a no-brainer.
If you're using a Synology NAS and are looking for a secure way to access your NAS via the internet, Tailscale is the way to go. Just make sure you disable QuickConnect after you're done switching.

Harish Jonnalagadda is Android Central's Senior Editor overseeing mobile coverage. In his current role, he leads the site's coverage of Chinese phone brands, networking products, and AV gear. He has been testing phones for over a decade, and has extensive experience in mobile hardware and the global semiconductor industry. Contact him on Twitter at @chunkynerd.
