Your privacy, fingerprints and the Fifth Amendment

January 2017: With the current political climate, we feel now is a great time to remind everyone about their right to privacy and where it ends. This post was originally published in May 2016 but it's just as important now, if not more so, than it was then.
Being able to unlock your phone with your fingerprints is a really good thing. It's not the most secure method you can use, and there are issues about having only one set of fingerprints if you ever need to change your login credentials, but the convenience factor means more people will keep their phones locked when they're not using them. That means your privacy is protected, as well as the privacy of everyone in your contacts or people you're networked with through social media when and if someone else gets their hands on your phone.
We all should thank Motorola for trying it, and Samsung and Apple for making it good. Biometrics used to verify identity isn't exactly new, but getting everything working on a tiny pocket computer surely wasn't easy. We've also seen Iris scanning on the Alcatel Idol 3 and short-lived Note 7. We'll probably be going through this same scenario when iris scanning tech takes off, too.

If you're in the U.S., though, there's another snag that not everyone knows about — law enforcement can force you to place your finger on your phone and unlock everything. A precedent was set by the Circuit Court of Virginia in October 2014, and recently upheld and reinforced by a federal court in February 2016, that makes it clear that while you can't be forced to provide a passcode for an electronic device, your fingerprints and using them to unlock the same device is not protected by the fifth amendment of the U.S. Constitution.
You can be forced to incriminate yourself by providing anything and everything on your phone to law enforcement by using your fingerprint as long as a warrant was requested and received. This will almost certainly be challenged as a direct violation of the fifth amendment (and possibly parts of the fourth amendment), but for now, this is the law.
You can be compelled to provide your fingerprint and unlock your phone, under current U.S. law
I want to be clear on a couple things here. Nobody at Android Central is condoning any criminal behavior, nor do we judge anyone for their feelings on how they want to help law enforcement investigate any case. If you want the U.S. government to have access to the data a person involved in an investigation has on their phone, that's fine. You should realize that not everyone feels the same way, as well as know that you don't have to be a law-breaker to value your privacy.
If you, or a peace officer in any capacity, would get access to my phone you'll find nothing that puts me at risk of prosecution, and probably be bored looking at pictures of my family and my dogs, see half-completed documents I'm working on and maybe an expense report or two. But that's my stuff, and I don't want anyone rifling through it. It's OK to feel differently.
Be an expert in 5 minutes
Get the latest news from Android Central, your trusted companion in the world of Android
But this leads us into ideas of how we can protect that privacy if we're using our fingers to open the secure container that holds it all. And there are a few things you can do.
You'll need a backup method to unlock your phone if you are using a fingerprint scanner. A four digit PIN works well here. It's not too difficult to break, but protections that make your wait between incorrect attempts and a self-destruct feature where data is wiped after a certain number of attempts mean that getting past a PIN will prove to be difficult. Like using a fingerprint in the first place, it's a nice balance between security and convenience.
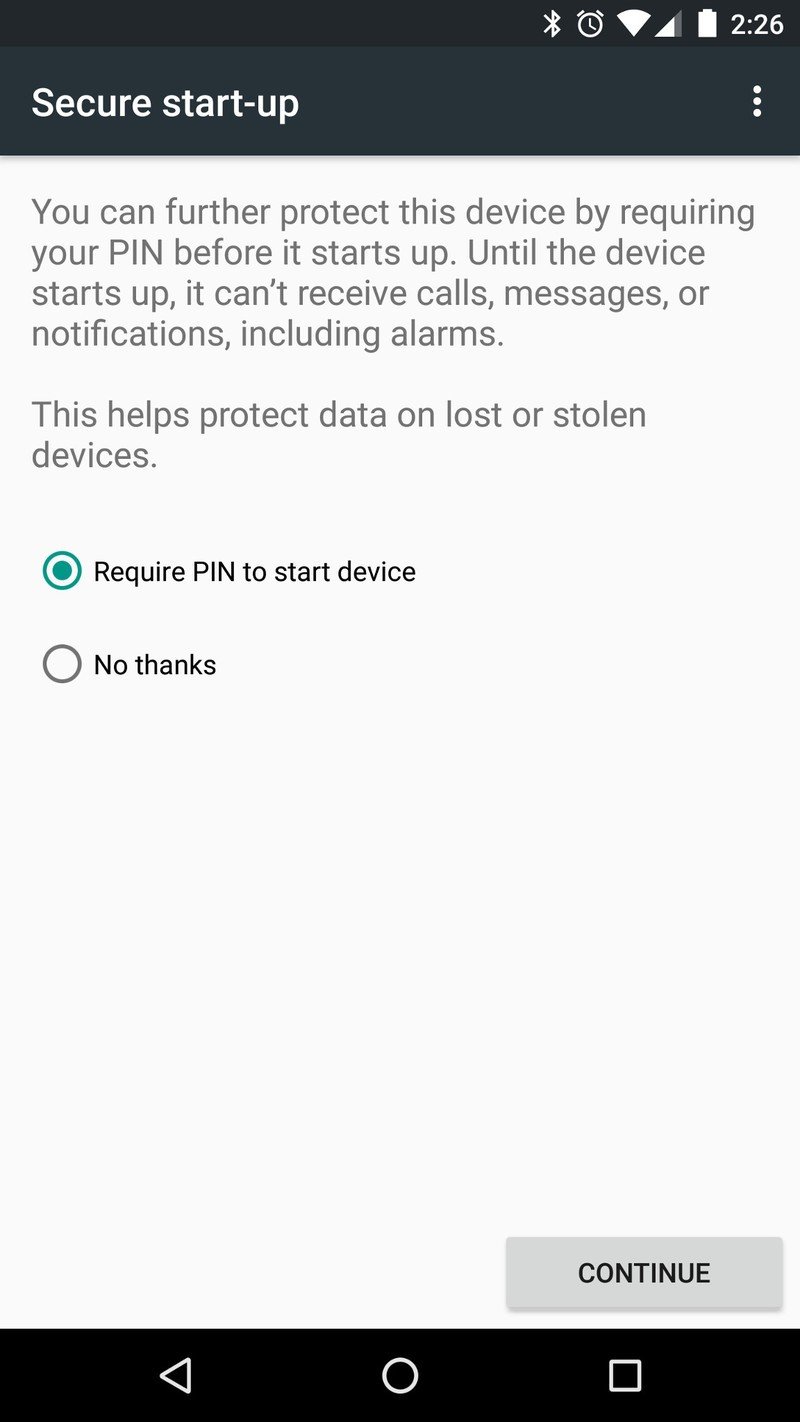
The real benefit here is that you can require this PIN to be entered before your phone will start. You'll see this option when you set up a phone as new, or when you go into the security settings and change the PIN itself. This means that every time your phone is started until the correct PIN is entered, it's completely dead. No data is decrypted, no calls can come in, and no software outside of the bootloader itself is running.
Because a PIN is either required to start the phone (if you choose to use this feature) or unlock the screen for the first time after it starts up, you can't unlock it with just your fingerprint — your fifth amendment protected PIN is required. And with all current Android phones and iPhones, a piece of hardware embedded in the system-on-chip that houses the CPU keeps things locked up and inaccessible through standard software hacking.
If you see the blue lights, just hold the power button and shut down your phone.
Now, this isn't going to help if you're a fugitive and subject to being detained on sight or caught in the act doing something shady. But if you're just a regular person who doesn't want anyone to get information about you or the people you keep company with it's pretty effective. If you're able to do this, it means you get to decide if you want to share what is on your phone with "the man."
If you see the blue lights, just hold the power button and shut down your phone.
Android phones with unlocked bootloaders also pose a risk. Don't think that even your local constable doesn't have access to people just as savvy with Android as the folks you find at XDA. If your bootloader is unlocked, anyone can dump the software and all the data from your phone onto a computer without ever having to use the lock screen. With enough incentive, even an encrypted image that has a key to unlock it stored in the protected hardware of the original phone can be cracked. Chances are there's not much incentive to go through this for a regular middle-aged dude like myself, but what if I had a random Twitter interaction with someone who is worth the trouble?
The internet connects the world, and that funny meme you liked on Facebook could have been posted by anyone. Facebook is obliged (rightfully so, in my opinion) to provide any and all publicly available data (the public part is important) about a user when the right warrant is served. If you liked a post from a person of interest, the people who want to know more about you don't care that you claim to have a phone filled with texts from your friends and cat pictures — they want to see for themselves. Keeping the bootloader locked means it's almost impossible for them to have a look, and they likely won't even try.
I want the police to put people doing horrible crimes in prison where they can be rehabilitated, or at least be kept from doing more harm to society. Most of us aren't one of those people, and getting arrested or detained for drag racing or having a tiny baggie of weed in your pocket or any other minor offense doesn't make you Charles Manson or the Zodiac Killer. Neither does peacefully protesting against a government overstepping their bounds. We all have rights and a reasonable expectation of privacy. If the courts won't decide to uphold our fourth and fifth amendment rights when it comes to what we have on our phones, then we should do everything we can to protect them ourselves.
I just want to share my data on my terms, and want the same for you.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.