Making sense of the latest Android 'Master Key' security scare
No spin, no bullshit, just clear simple talk about what's going on this time
Some real talk about this exploit that the Bluebox security team discovered is needed. The first thing to know is that you’re probably affected. It’s an exploit that works on every device that’s not been patched since Android 1.6. If you’ve rooted and ROM'd your phone, you can freely ignore all of this. None of this counts for you, because there is a whole different set of security concerns that comes with root and custom ROMs for you to worry about.
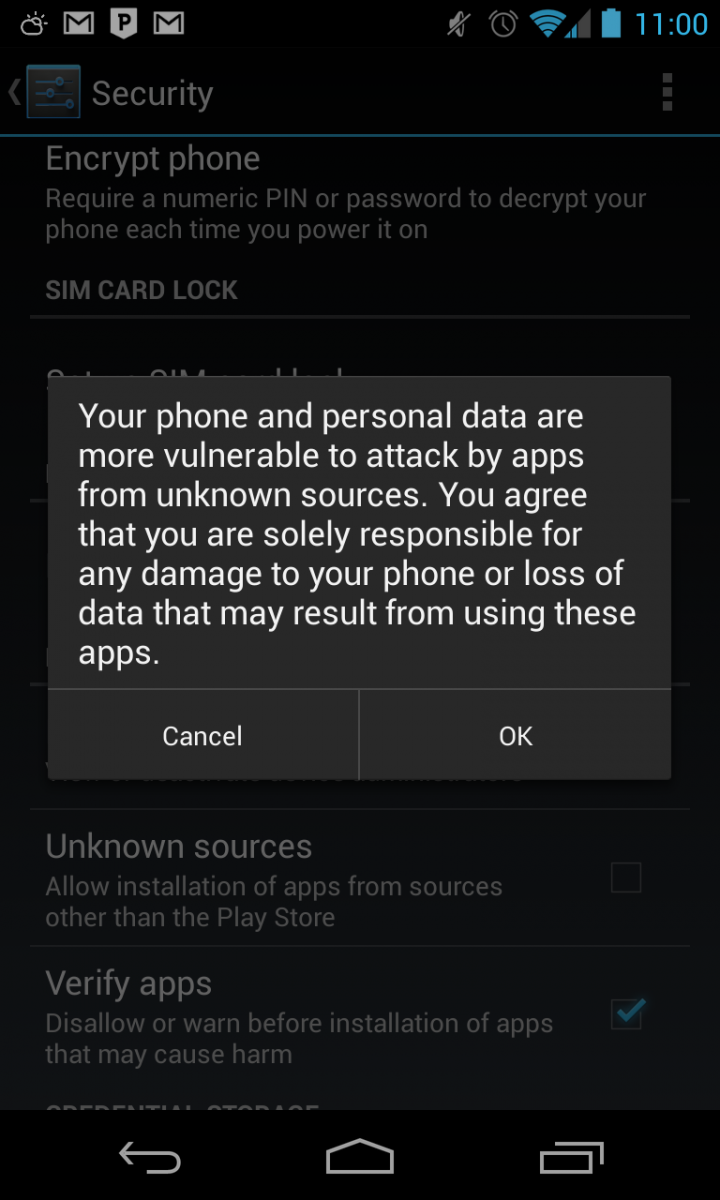
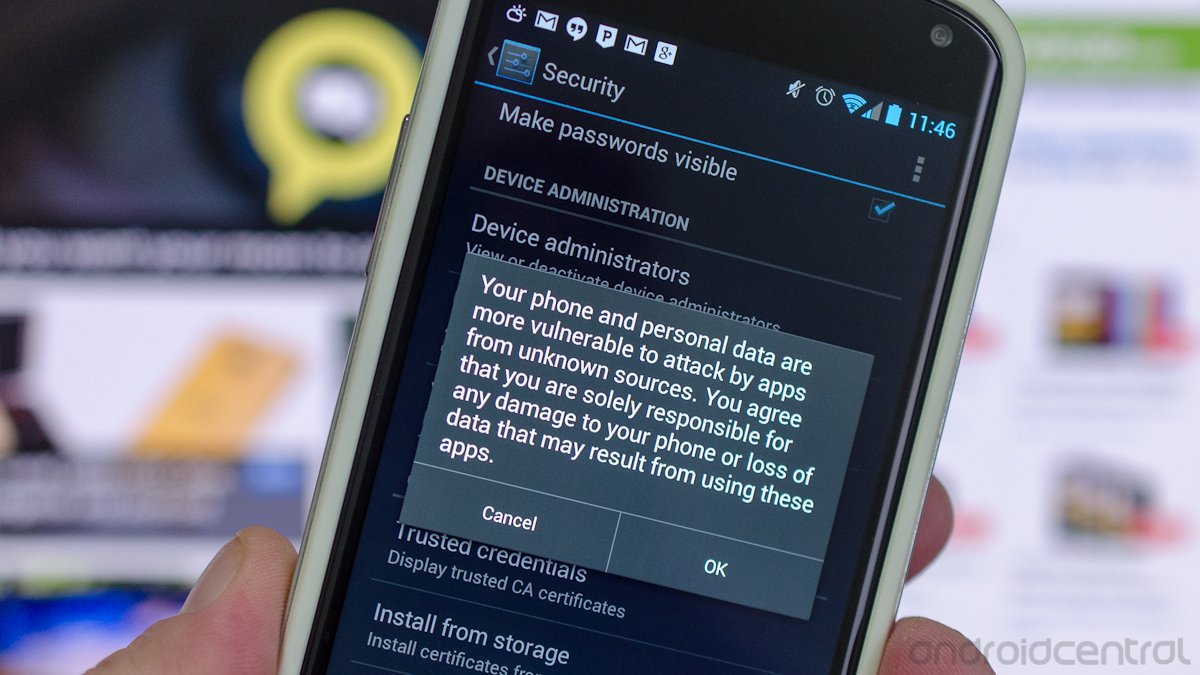
If you don’t have the infamous “Unknown Sources” permission box checked off in your settings, this all means nothing to you. Carry on, and feel free to be a little smug and self-righteous — you deserve it for eschewing sideloading all this time in case something like this could happen. If you don't know what this means, ask someone.
For the rest of us, read past the break.
More: IDG News Service.
Special thanks to the whole Android Central Ambassador team for helping me make sense of this!
What is it?
Get the latest news from Android Central, your trusted companion in the world of Android
All apps on your Android are signed with a cryptographic key. When it’s time to update that app, the new version must have the same digital signature as the old or it won’t overwrite. You can't update it, in other words. There are no exceptions, and developers who lose their signing key have to create a brand new app that we have to download all over again. That means starting from zero. All new downloads, all new reviews and ratings. It's not a trivial matter.
The system apps — the ones that came installed on your phone from HTC or Samsung or Google — also have a key. These apps often have complete administrator access to everything on your phone, because they are trusted apps from the manufacturer. But they're still just apps.
Still following me?
What we're talking about now, what Bluebox is talking about, is a method to tear open an Android app and change the code without disturbing the cryptographic key. We cheer when hackers get around locked bootloaders, and this is the same sort of exploit. When you lock something, others will find a way in if they try hard enough. And when your platform is the most popular on the planet, people try very hard.
So, someone can take a system application from a phone. Just pull it right out. Using this exploit, they can edit it to do nasty things — give it a new version number, and pack it back together while keeping the same, valid signing key. You could then potentially install this app right overtop your existing copy, and you now have an app designed to do bad things and it has complete access to your entire system. The whole time, the app will look and behave normally — you’ll never know something fishy is going on.
Yikes.
What’s being done about it?
The folks at Bluebox told the entire Open Handset Alliance about this back in February. Google and OEMs are responsible for patching things to prevent it. Samsung did its part with the Galaxy S4, but every other phone they sell is vulnerable. HTC and the One didn’t make the cut, so all of HTC’s phones are vulnerable. In fact, every phone except the Samsung Touchwiz version Galaxy S4 is vulnerable.
Google hasn’t yet updated Android to patch this issue. I imagine they're working hard on it — see the issues Chainfire has went through rooting Android 4.3. But Google didn’t sit idly by and ignore it either. The Google Play store has been “patched” so that no tampered apps can be uploaded to Google’s servers. That means any app you download from Google Play is clean — at least where this particular exploit is concerned. But places like Amazon, Slide Me, and of course all those cracked APK forums out there are wide open and every application could have bad JuJu inside it.
So this is a really big deal?
Yes it’s a huge deal. And at the same time, no, it’s really not.
Google will patch the way Android updates apps or the way they are signed. In this cat-and-mouse game, this is a normal occurrence. Google releases software, hackers (both the good kind and the bad kind) try to exploit it, and when they do Google changes the code. That’s how software works, and this sort of thing should be expected when you have enough smart people trying to break in.
On the other hand, the phone you have now may not ever see an update to fix this. Hell, it took Samsung almost a year to patch the browser against an exploit that could erase all your user data on just some of its phones. If you have a phone that you expect to be updated to Android 4.3, you will probably get patched. If not, it’s anybody’s guess. That’s bad — very bad. I'm not trying to slag on the people who make our phones, but truth is truth.
What can I do?
- Don't download any apps outside of Google Play.
- Don’t download any apps outside of Google Play.
- Don't download any apps outside of Google Play.
- In fact, go ahead and turn off the Unknown Sources permission if you like. I did. Anything else leaves you vulnerable. Some “Anti-Virus” apps will check if you have unknown sources enabled if you’re not sure. Get into the forums and find out which one everyone says is the best if you need to.
- Express your displeasure at not getting essential security updates for your phone. Especially if you’re still on that two-year (or three-year — hello Canada!) contract.
- Root your phone, and install a ROM that has some sort of fix -- the popular ones will likely have on very soon.
So don’t panic. But be proactive and use some common sense. Now is a really good time to stop installing cracked apps, because the people doing the cracking are the same sort of people who could put evil code into the app. If you get any update notices that come from a place other than Google Play, tell somebody. Tell us if you need to. Figure out the people who are trying to pass on these exploits and give them a heavy dose of public shaming and exposure. Cockroaches hate the light.
This will pass like security scares always do, but another will step in to fill its shoes. That’s the nature of the beast. Stay safe guys.

Jerry is an amateur woodworker and struggling shade tree mechanic. There's nothing he can't take apart, but many things he can't reassemble. You'll find him writing and speaking his loud opinion on Android Central and occasionally on Threads.